Leveraging Machine Learning Algorithms
Leveraging Machine Learning Algorithms for Enhanced Efficiency
Industries worldwide are experiencing a paradigm shift thanks to machine learning algorithms, which automate intricate tasks and refine decision-making. These algorithms excel at spotting patterns and forecasting outcomes from massive datasets, enabling businesses to streamline operations, cut expenses, and outpace competitors. This leap in efficiency directly boosts profits and elevates customer experiences. From predictive maintenance in factories to tailored suggestions in online shopping, machine learning's applications are boundless.
By handling mundane tasks, machine learning liberates human talent for strategic endeavors. This redirection sparks innovation and equips businesses to navigate fluctuating markets with agility. Moreover, sifting through extensive data reveals hidden trends, paving the way for groundbreaking products and services.
Types of Machine Learning Algorithms Used
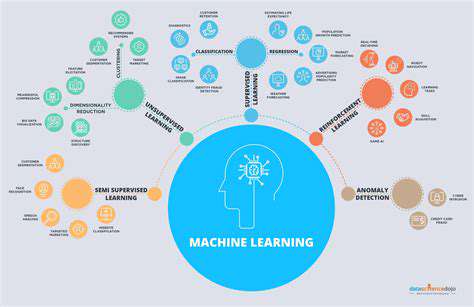
Diverse machine learning algorithms cater to different needs. Supervised learning models, like linear regression and support vector machines, thrive on labeled data to predict results. Unsupervised learning counterparts uncover structures in raw data, aiding in customer grouping and anomaly spotting. Meanwhile, reinforcement learning iteratively refines actions to hit targets. Each algorithm family serves distinct purposes across applications.
Selecting the right algorithm demands understanding their intricacies. The decision hinges on data characteristics, desired outputs, and available computing power. Thoughtful evaluation of these elements guarantees peak performance and maximizes machine learning's return on investment.
Real-World Applications of Machine Learning
Machine learning is reshaping industries. Healthcare leverages it for early disease detection and customized treatments. Financial institutions deploy it to flag fraudulent activities and sharpen credit assessments. Factories employ it to anticipate machine breakdowns and fine-tune production lines. These instances showcase machine learning's capacity to solve intricate problems sector-wide.
Such applications underscore machine learning's adaptability. Whether refining business workflows or enhancing choices, it empowers organizations to achieve remarkable efficiency gains. With continuous algorithmic evolution, even greater breakthroughs loom on the horizon.
Data Preparation and Feature Engineering
Flawless data preparation precedes successful machine learning implementation. This meticulous process involves cleansing, reformatting, and conditioning data for analysis. Cleaning addresses gaps, anomalies, and inconsistencies, while transformation adapts data for algorithmic consumption. Feature engineering crafts new variables from existing ones to boost model precision. Rigorous data preparation underpins trustworthy machine learning outcomes.
Feature engineering represents a pivotal phase in model development. It extracts meaningful signals from raw data and constructs variables that capture complex relationships. This art demands both domain knowledge and data intuition. Masterful feature engineering unlocks superior predictive power and deeper analytical insights.
Ethical Considerations and Bias Mitigation
Machine learning's expansion brings ethical dilemmas to the fore. Since models learn from historical data, they risk perpetuating societal prejudices present in their training material. This serious concern demands proactive solutions. Ensuring fairness and inclusivity in machine learning systems is non-negotiable for responsible implementation. Vigilant bias detection and correction in both data and models prevent harmful unintended effects.
Transparency and interpretability form the bedrock of ethical machine learning. Knowing how models reach conclusions fosters trust and accountability. Crafting models that balance effectiveness with explainability is paramount for earning public confidence and upholding ethical standards.
Security Considerations and Future Trends
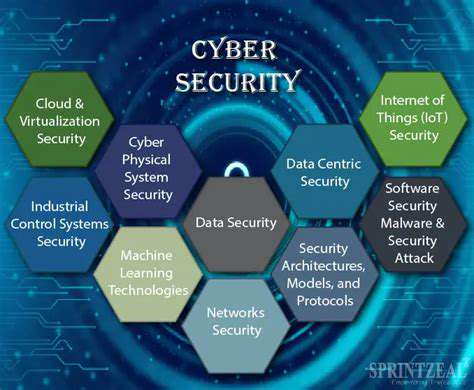
Implementing Robust Security Measures
Contemporary applications demand comprehensive security frameworks. Effective protection extends beyond firewalls to include layered defenses like access management, encryption protocols, and routine security evaluations. Potential weak points require systematic identification and remediation. This holistic strategy safeguards sensitive information's confidentiality, integrity, and accessibility.
Security testing must integrate throughout development cycles. Penetration tests, vulnerability assessments, and code inspections are indispensable for uncovering and fixing flaws preemptively. Staying ahead of threats ensures application resilience against evolving cyber risks.
Future-Proofing the Application
Application longevity requires anticipating digital evolution. This means preparing for emerging attack vectors, shifting user demands, and technological progress. Adaptability ensures continued relevance and security. Scalable, flexible architectures form the cornerstone of future-ready systems.
Data Encryption and Protection
Sensitive data demands ironclad protection. Implementing end-to-end encryption—for both transmitted and stored information—is non-negotiable. This renders intercepted data useless without decryption keys, dramatically reducing breach impacts. Such measures form critical barriers against unauthorized access.
User Authentication and Authorization
Stringent access controls are imperative for sensitive systems. Multi-factor authentication, robust password requirements, and granular permission systems work in concert. These measures ensure that only properly credentialed users reach protected resources. This layered approach significantly diminishes unauthorized access risks.
Regular Security Audits and Updates
Ongoing security maintenance is essential. Periodic vulnerability scans, coupled with timely software patches, maintain defensive postures. Consistent audits and updates represent proactive defenses against potential exploits. Adhering to security best practices minimizes exposure to threats.
Incident Response Planning
Preparedness separates minor incidents from catastrophic breaches. Detailed response blueprints should outline detection, containment, and recovery protocols. This forward-thinking approach enables swift, effective reactions to security events, minimizing operational disruption. Well-practiced incident response can dramatically reduce breach fallout.
