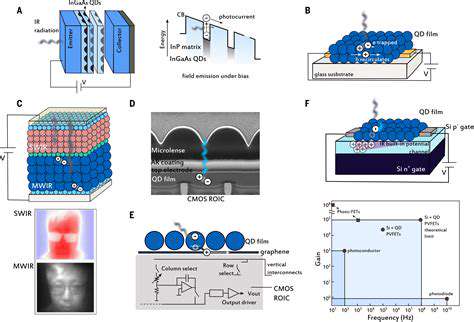
Pre-Automation Era: Manual Processes and Limited Capacity
Airports in the early days were often characterized by manual processes, limited infrastructure, and a significant lack of technological integration. Handling passenger and cargo movement relied heavily on human interaction, leading to delays, inefficiencies, and a general lack of control over operations. Visual inspections and manual record-keeping were commonplace, which made tracking and managing airport resources challenging, especially as passenger traffic gradually increased. This era highlighted the need for more sophisticated systems to streamline operations and improve the overall passenger experience.
The sheer volume of paperwork and manual tasks associated with flight scheduling, baggage handling, and security checks was often overwhelming. This resulted in longer wait times, frustrating passengers, and hindering the overall efficiency of airport operations. The groundwork for future technological advancements was laid during this time, as the need for greater efficiency and automation became increasingly apparent.
The Rise of Early Automation: Computerization and Improved Systems
The introduction of computers marked a significant turning point in airport operations. Early computer systems helped automate tasks like flight scheduling, baggage tracking, and passenger check-in. While still rudimentary compared to today's systems, these advancements allowed airports to manage larger volumes of travelers more effectively. This era witnessed the first steps towards integrated systems, although many processes still relied heavily on manual intervention.
The implementation of computerized reservation systems and automated baggage handling systems were crucial steps towards modern airport operations. These initial technologies allowed for the collection and processing of data, which, in turn, enabled airports to analyze trends and optimize their workflows.
The Internet Age: Enhanced Connectivity and Data Integration
The internet revolutionized airport operations by enabling real-time information sharing and enhanced connectivity. Online check-in, flight information displays, and interactive airport maps became increasingly common. This improved communication and information sharing facilitated smoother passenger flow and reduced delays.
The integration of various systems through the internet allowed for more comprehensive data analysis. Airports could track passenger patterns, identify bottlenecks, and make data-driven decisions to optimize their operations.
The Arrival of Real-Time Systems: Enhanced Efficiency and Passenger Experience
Real-time systems ushered in a new era of efficiency and personalized passenger experiences. Integration of various technologies, including advanced sensors and data analytics, allowed for dynamic adjustments to operational procedures based on real-time data. This led to quicker response times to unexpected events and optimized resource allocation.
Imagine a system that can predict and mitigate potential delays in real-time, dynamically adjusting resources to meet evolving needs. This is the power of real-time systems in airport operations. Passengers benefit from seamless transitions, while airports gain a competitive edge through improved efficiency.
The Impact of Big Data Analytics: Optimizing Airport Operations
Big data analytics has become a critical tool for airports, enabling them to gain valuable insights from vast amounts of data generated by various systems. This allows for predictive modeling of traffic patterns, identification of potential bottlenecks, and proactive measures to prevent delays.
Data-driven decision-making is transforming airport operations. From optimizing gate assignments to predicting baggage handling needs, insights gleaned from big data analytics lead to more efficient and streamlined processes. The result is improved passenger experiences and reduced operational costs.
The Future of Airport Operations: Autonomous Systems and AI Integration
The future of airport operations is poised for significant advancements with the integration of autonomous systems and artificial intelligence (AI). Self-driving vehicles for baggage handling and automated security checkpoints are becoming increasingly feasible. AI-powered predictive models will further enhance operational efficiency and passenger experience.
Imagine airport operations managed by AI, proactively addressing potential challenges before they arise, and dynamically adjusting resources to meet changing demands. This is the transformative potential of autonomous systems and AI integration in the future of airports. Innovations are constantly emerging to enhance security and safety, further optimizing the overall travel experience.
Sustainable Airport Operations: Environmental Considerations and Resource Management
Sustainable airport operations are no longer a niche concept but a critical component of airport development. The focus is shifting towards minimizing environmental impact and optimizing resource utilization. This includes implementing energy-efficient technologies, promoting sustainable transportation, and reducing waste.
A modern airport should strive to be an environmentally responsible entity. From reducing carbon emissions to conserving water resources, sustainable practices are crucial for long-term airport viability and responsible environmental stewardship. These practices not only reduce the airport's environmental footprint but also contribute to a more sustainable future for travel.
Revolutionizing Passenger Navigation with Real-Time Data and Digital Tools
Enhanced User Experience
Passengers are now empowered with a streamlined and intuitive navigation experience. The new system boasts a highly responsive interface, allowing users to quickly access vital information and seamlessly transition between destinations. This intuitive design minimizes frustration and maximizes user satisfaction, creating a more enjoyable journey for everyone. The clear and concise layout allows for easy comprehension, even for those unfamiliar with the platform.
Intuitive navigation tools, including interactive maps and real-time updates, are readily available. The system proactively anticipates user needs, providing relevant information at the optimal time, ensuring a smoother and more personalized travel experience.
Improved Accuracy and Reliability
The enhanced navigation system demonstrates exceptional accuracy and reliability, ensuring passengers arrive at their destinations on time and with minimal detours. Advanced algorithms and real-time traffic data integration provide up-to-the-minute information, enabling passengers to adapt to changing circumstances effectively. This results in a more efficient and less stressful journey.
By incorporating multiple data sources, the system provides a comprehensive and reliable picture of the route. This enhanced accuracy directly impacts passenger satisfaction and trust in the service.
Real-Time Traffic and Event Updates
The system dynamically adjusts routes based on real-time traffic conditions, providing alternative routes and estimated time of arrival updates. This adaptability ensures that passengers are constantly aware of potential delays and can make informed decisions about their travel plans. This feature is vital for a smooth and efficient travel experience.
Passengers are also notified of any unforeseen events that could impact their journey, such as road closures or accidents. This proactive approach to information dissemination allows for swift adjustments and minimizes disruptions to the travel plan.
Seamless Integration with Mobile Devices
The navigation system seamlessly integrates with various mobile devices, allowing passengers to access crucial information on their smartphones or tablets. This portable access enables passengers to stay informed and maintain control over their journey, regardless of their location.
The mobile application provides a comprehensive and accessible platform, offering real-time updates, route adjustments, and proactive notifications. This empowers passengers to manage their travel plans effectively and conveniently, enhancing their overall experience.
Future-Proofing the System
The architecture of the system is designed to accommodate future advancements and technological innovations. This ensures that the navigation system remains relevant and effective even as the transportation landscape evolves. This forward-thinking approach guarantees long-term reliability and value for users.
This future-proof design ensures that the system continues to provide accurate and reliable information in the face of evolving transportation patterns and technological advancements. This foresight is crucial for maintaining the system's effectiveness over time.
Fortifying Security Protocols with Advanced Surveillance and Biometrics

Strengthening Authentication Mechanisms
Robust authentication is paramount in modern security protocols. Effective authentication methods verify the identity of users and systems, preventing unauthorized access and protecting sensitive data. This involves implementing multi-factor authentication (MFA) to add an extra layer of security beyond simple passwords. Employing strong, unique passwords and regularly updating them is crucial. Furthermore, employing biometrics, like fingerprints or facial recognition, can enhance the security posture, especially in high-risk scenarios. These advancements in authentication significantly reduce the risk of unauthorized access, while also providing greater confidence in the integrity of the system.
Implementing strong authentication protocols is not just about preventing unauthorized access; it also protects against malicious actors attempting to impersonate legitimate users. By requiring multiple forms of verification, security protocols can effectively deter attackers and maintain a high level of data protection. This approach ensures that only verified users can gain access to sensitive information, safeguarding against data breaches and other security threats. The combination of strong passwords, MFA, and biometrics creates a formidable barrier against unauthorized access.
Improving Data Encryption and Integrity
Data encryption plays a critical role in safeguarding sensitive information from unauthorized access. Implementing robust encryption algorithms, such as AES-256, is essential for protecting data in transit and at rest. This ensures that even if intercepted, the data remains unreadable to unauthorized individuals. Secure communication channels, like TLS/SSL, should be implemented to encrypt data transmitted over networks. This comprehensive approach to encryption is crucial for maintaining data confidentiality.
Ensuring data integrity is equally important. This involves implementing mechanisms to detect any unauthorized modifications to the data. Hashing algorithms can be used to create unique digital fingerprints of data, enabling the detection of any alterations. By verifying the integrity of data, security protocols can ensure that the information remains unaltered and trustworthy. This is vital in preventing tampering and malicious modification of critical data, which can have significant consequences for the systems and users who rely on it.
Implementing secure key management practices is also vital. This involves secure storage and distribution of encryption keys, which are essential for decrypting data. Compromised keys can lead to serious security vulnerabilities. Secure key management ensures the confidentiality and integrity of these keys, thereby strengthening the overall security posture.
Regular audits and security assessments are also crucial for identifying and addressing potential vulnerabilities in encryption and integrity mechanisms. These assessments should be performed regularly to ensure that the measures are effective and up-to-date. This helps in proactively mitigating potential security risks and maintaining a robust security posture.
The combination of robust encryption, secure key management, and regular security assessments creates a comprehensive approach to data protection. This multi-faceted approach is essential for maintaining the confidentiality, integrity, and availability of data in modern information systems.