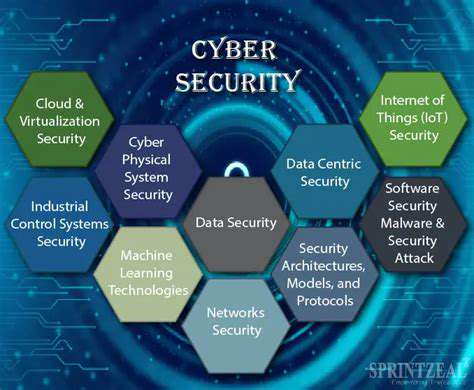
Critical Aspects of Data Privacy and Regulatory Adherence

Strategic Data Reduction
The principle of data minimization serves as the cornerstone of privacy preservation. Organizations must strictly collect only essential information required for operational purposes. This disciplined approach dramatically decreases exposure to security incidents while fostering transparent data stewardship. Beyond risk mitigation, this philosophy inherently limits opportunities for data exploitation.
Businesses should conduct regular data audits to identify redundant information. Obsolete records should undergo secure destruction or anonymization processes. Such practices not only comply with regulations but also demonstrate organizational commitment to privacy protection.
Comprehensive Protection Protocols
Implementing enterprise-grade security measures remains non-negotiable for sensitive data protection. Advanced encryption standards must safeguard information during transmission and storage. Multi-layered authentication systems create formidable barriers against unauthorized access attempts. Proactive security evaluations help identify system vulnerabilities before exploitation occurs.
Granular access controls ensure only vetted personnel handle confidential data. Continuous employee education programs maintain awareness of evolving security protocols and threat landscapes.
Clear Communication Practices
Establishing transparent data policies builds consumer confidence and regulatory compliance. Organizations must articulate collection purposes, data categories, and access parameters in accessible language. Explicit consent mechanisms should empower users with genuine control over their personal information.
Consent forms should avoid complex legal jargon, instead providing clear options for data usage preferences. This ethical approach respects individual autonomy while satisfying legal requirements.
Regulatory Alignment
Navigating the complex landscape of data protection laws requires dedicated compliance efforts. Organizations operating across jurisdictions must understand regional variations in privacy statutes. Implementing adaptable compliance frameworks ensures readiness for evolving regulatory environments.
Regular policy reviews and updates maintain alignment with new legislation. Designated compliance officers can oversee implementation of data subject rights processes.
Incident Preparedness
Developing robust breach response protocols minimizes damage from security incidents. Detailed plans should outline notification timelines, forensic procedures, and containment strategies. Prepared organizations experience significantly reduced reputational harm during security crises.
Simulation exercises test response effectiveness, while post-incident reviews identify improvement opportunities. Transparent communication with affected parties demonstrates accountability.
Cross-Border Data Governance
International data flows necessitate specialized legal considerations. Transfer mechanisms must account for varying protection standards across jurisdictions. Standard contractual clauses and binding corporate rules often provide compliant transfer solutions.
Continuous monitoring of geopolitical developments ensures ongoing compliance with evolving international data transfer regulations.
Evolution of Edge Computing Architectures

Scalability Advancements
Distributed computing paradigms fundamentally transform data processing capabilities. Geographic dispersion of compute resources alleviates traditional cloud bottlenecks. This architectural shift enables exponential growth in data handling capacity without compromising performance.
Industrial applications particularly benefit from localized processing, where milliseconds impact operational safety. The elimination of round-trip cloud communications unlocks new possibilities for data-intensive applications.
Adaptive System Design
Modern edge solutions demonstrate unprecedented flexibility across diverse use cases. Proximity-based processing enables sub-second response times for critical applications. Autonomous systems leverage this capability for split-second decision making without cloud dependency.
The architecture's inherent versatility supports multimodal data processing, from IoT sensor streams to high-definition video feeds. This adaptability future-proofs investments against evolving technological requirements.
Performance Optimization
Latency-sensitive applications achieve transformative improvements through edge deployment. Localized data processing eliminates network-induced delays for mission-critical operations. End-users experience tangible quality enhancements in interactive applications and media services.
Real-time analytics capabilities enable immediate operational adjustments in manufacturing and logistics. The combination of reduced latency and distributed intelligence creates new paradigms for responsive system design.