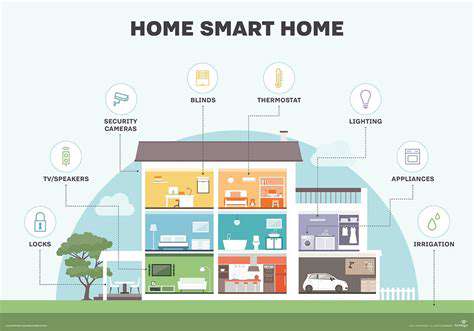
Real-Time Monitoring and Control with IoT

Real-Time Data Acquisition
Modern monitoring systems depend on uninterrupted data streams gathered from diverse sources. Parameters like temperature fluctuations, pressure variations, and sensor outputs must be captured and analyzed immediately to enable swift reactions and precise adjustments. The efficiency and dependability of this information-gathering mechanism directly impact the success of any instantaneous monitoring solution. Precise, time-sensitive measurements form the basis for smart choices and quick adaptations to dynamic situations.
Various sensors produce information at different frequencies, necessitating advanced processing frameworks to handle the continuous flow. These systems must demonstrate both resilience and expandability to support future requirements and increasing complexity. Proper data collection serves as the cornerstone for all effective real-time surveillance and management implementations.
Control System Architecture
An intelligently designed control framework is vital for managing massive datasets and executing efficient management protocols. Such structures should incorporate flexibility and growth potential to allow for future enhancements. Carefully planned system organization guarantees smooth interaction between components and optimizes information exchange across the control network.
Many implementations adopt segmented design approaches to improve adaptability and serviceability. This compartmentalization enables straightforward component replacement or improvement without affecting overall operations. Such features prove particularly valuable in intricate setups requiring regular updates and modifications.
Control Algorithms
Advanced processing routines are indispensable for interpreting instantaneous measurements and generating suitable corrective measures. These mathematical models dictate system reactions to environmental changes, maintaining desired operational standards. The precision and agility of these computational methods significantly influence the overall performance of continuous monitoring solutions.
Various approaches including proportional-integral-derivative regulation, approximate reasoning systems, or artificial neural networks may be selected based on application demands. Choosing appropriate computational models is essential for achieving peak efficiency and stability in feedback loops. The selected methods should demonstrate capacity to adjust to system fluctuations and unexpected disturbances.
Data Visualization and Reporting
Intuitive graphical representation and documentation are crucial for interpreting collected metrics and spotting potential concerns. Live information displays and analytical summaries offer comprehensive performance snapshots, helping technicians quickly recognize and resolve abnormal conditions. Well-designed graphical interfaces play a vital role in prompt situational assessment and maintaining ideal operational parameters.
Interactive panels allowing detailed metric examination prove especially useful for thorough investigation and problem diagnosis. These interfaces should feature customization options to satisfy diverse organizational requirements and user responsibilities.
Fault Detection and Diagnosis
Continuous surveillance solutions must incorporate comprehensive anomaly identification and troubleshooting features. These capabilities enable detection of irregularities or malfunctions, permitting preventive actions and avoiding potential operational interruptions. Timely recognition of system abnormalities is fundamental for reducing downtime and preserving equipment reliability.
Advanced analytical methods can examine data patterns to uncover potential failures. These techniques can also forecast future issues using historical trends and current indicators, facilitating preventive maintenance planning. This forward-looking strategy for problem detection and resolution is critical for optimizing performance and controlling expenses.
Security Considerations
Continuous monitoring networks frequently involve confidential information and vital infrastructure. Protection against unauthorized access and digital threats must be prioritized. Stringent protective protocols are necessary to safeguard system integrity and data privacy.
Deploying rigorous verification procedures along with periodic security evaluations is essential. Regular updates to protective software and policies help counter emerging threats. Information encryption and protected transmission pathways represent fundamental elements of thorough security planning.
Enhanced Security and Public Safety
Enhanced Security Measures
Implementing comprehensive protective strategies is essential for maintaining community security. These approaches should incorporate multiple dimensions, including upgraded observation networks, better illumination in communal areas, and additional security personnel in vulnerable locations. Strategic investment in emerging technologies like biometric identification systems (when applied ethically) can dramatically improve criminal identification processes. Additionally, neighborhood participation initiatives and local business collaborations can cultivate shared accountability, enhancing area security.
Critical aspects of improved protection include continuous training for security personnel with modern methodologies. This encompasses specialized instruction in conflict resolution, emergency response, and diverse scenario management. Regular equipment upgrades featuring current technology such as wearable recording devices and advanced communication gear ensure preparedness for various situations.
Public Safety Initiatives
Advancing community security requires more than reactive strategies. Preventative programs focusing on social welfare and education hold equal importance. Such efforts might involve adolescent development activities, addiction prevention campaigns, and vocational training opportunities. Addressing underlying societal factors and creating constructive pathways can establish more secure and thriving communities.
Educational efforts significantly influence responsible citizenship. Information campaigns regarding emergency procedures, transportation rules, and personal protection methods empower individuals to take preventive actions. This anticipatory method, combined with community reinforcement, can substantially decrease incident probabilities and promote safety-conscious attitudes.
Public Awareness and Engagement
Effective information sharing and community interaction are fundamental for building security awareness and mutual trust. Consistent communication methods including local forums, digital updates, and informational broadcasts provide current details and address public questions. This openness helps establish confidence between residents and protective services.
Encouraging citizen participation in security programs is paramount. Options might include local surveillance groups, volunteer patrols, or initiatives supporting community-oriented policing. Engaging residents directly in protective measures allows them to contribute actively to neighborhood safety. Community input offers valuable perspectives and promotes collective responsibility for maintaining secure environments.
Clear policies and accessibility of information regarding security procedures strengthen public confidence. Established channels for reporting concerns and addressing complaints enhance transparency within protective services. Constructive communication and proactive issue resolution will reinforce relationships between communities and their protective services.